Safety on the internet — that is, protecting your computer from malware — used to be as simple as not downloading and running dodgy executable code. Sure, some people were tricked, either via emails from “friends” or popups trying really hard to convince them to run a local binary.
Websites that wanted to provide a richer experience had a few options: run ActiveX controls in IE — the notion of letting a binary run because a website told it to seemed stupid even at the time, even with the idea of “signed” ActiveX controls, so you’d know who provided a control. There was Flash, a proprietary binary and scripting language now owned by Adobe, and then there was Java, which ran in its own virtual machine with limited access, which seemed like the saner of all the options.
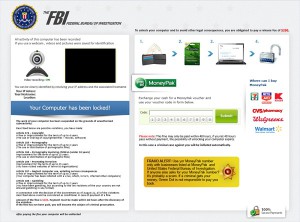
Recently, I stayed in a hotel where the first thing I did was poke through some of my history, looking for an article I’d been reading before — which I located, and about a paragraph in, my screen was entirely replaced with a (fake) FBI warning and a demand to pay a “release fee” of $200 to regain control of my computer. This was accompanied by the hotel’s IP address, and a display window that was apparently supposed to turn on the PC’s camera and show me in my underwear.
This is known as the “FBI Green Dot Moneypak” scam, or the “FBI Moneypak Virus,” which actually covers a large family of extortionware — which is essentially a monetizing payload, like this scam, plus a way to deliver it to your computer. In my case, the delivery mechanism appears to be a Java exploit, triggered by either a malicious ad from a site I’d visited before (at home we use a proxy that strips out suspicious ads, so it’s possible it had been there before, but my PC wasn’t actually infected until I visited the same site from the hotel.)
In my case, the infection was completely missed by malware scanners, which seemed to think that my PC was perfectly fine, and even ad hoc scanners proved relatively useless — even a few which claimed to be able to detect and remove this (detection is free, removal requires payment) were blissfully unaware that the infection had taken place. Googling wasn’t a lot of help either, since I was either directed to sites with generic instructions to run whatever scanner they were hocking (none of which worked) or long lists of registry keys to check, none of which appeared to exist on my system. So it was either hiding itself well, or too recent to be picked up by scan-based systems.
At any rate, since it was Windows 7, I was able to “switch user” to an Administrator account, and I since I hadn’t received a request to escalate permissions, chances were relatively good it hadn’t inserted itself too deeply into my OS. I found two suspicious binaries — suspicious, because they weren’t where binaries typically go: in c:\ProgramData was “lsass.exe” and in c:\Users\username\AppData\Local\Temp was “ctfmon.exe.” Both of these are legitimate Windows binaries that would be run — lsass.exe, for example, is the Local Security Authority Subsystem Service, a legitimate version pretty much needs to be running or the system will restart, and ctfmon.exe activates the language bar. Since I generally have that turned off, this is pretty suspicious, but even more suspicious is the location of these files. Deleting them in safe mode (from an alternative account) cleared the infection, returning control of my PC. The PC complained about not being able to find a few files it wanted to run on startup, but I considered that a good sign.
Meanwhile, I went back to my browser to examine the source of the infection, and surely enough, a Java plugin was enabled — and since it’s the only thing enabled, it’s pretty obvious that this was the source of the problem.
If you haven’t done so already, I’d recommend disabling your Java plugins (virtually no Internet site uses it any more) and any other plugins which you don’t actually need. If you do use Flash, which is relatively hard to avoid, at least make sure it’s up to date. Note that updating the version of Flash doesn’t necessarily update the plugin version, so check from within your browser, not just by looking at versions in the Control Panel.
Mozilla has a handy URL that actually works across browsers:
https://www.mozilla.org/en-US/plugincheck/